Cybercriminals Seek Profit in Coronavirus
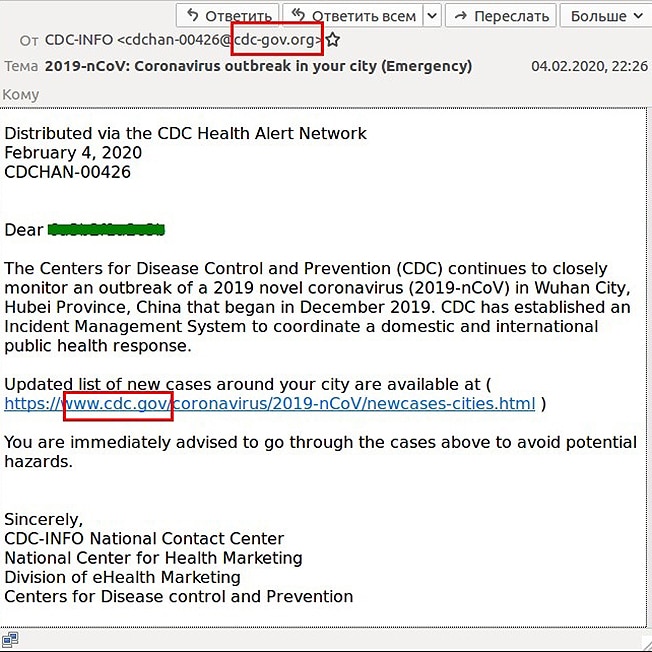
WASHINGTON — An email seemingly from the U.S. Centers for Disease Control and Prevention warns of new coronavirus infections and urges readers to click on a link to see a list of infections in their community.
But the email actually comes from cybercriminals looking to use the crisis to their advantage.
Cybersecurity researchers have identified a growing number of phishing scams in which fraudsters are using coronavirus to entice victims. With phishing, recipients unwittingly click on emailed or texted links designed to trick them into giving their personal information.
“It is the most clickable lure that an attacker can send out. Everyone has jumped on the bandwagon,” said Ryan Kalember, an executive vice president at Proofpoint, a global cybersecurity company that is monitoring the phishing activity. “Their success depends on getting people to click. Coronavirus drives clicks like nothing else right now.”
Officials in some states have alerted government staffers and the public about that threat. And some states have stepped up monitoring for malicious email involving coronavirus.
In Washington state, the nation’s epicenter of coronavirus, with 366 confirmed cases and 29 deaths as of Thursday, the top information security official issued a warning to staffers and the public to be on the lookout for such threats.
Bad actors are using phishing emails that claim to have information about coronavirus infections in the surrounding area and encourage users to click on a link or an attachment to find out more, Vinod Brahmapuram, the state chief information security officer, wrote in a recent blog post.
“Attackers create a sense of urgency, of panic, almost forcing people to take action. The coronavirus gives them an advantage,” Brahmapuram said in an interview with Stateline. “It’s new. It’s unknown. When there is something unknown, the fear is so high.”
In Connecticut, information technology officials have asked the state’s emergency management department to spread the word about phishing scams related to coronavirus, Chief Information Officer Mark Raymond said.
And in Virginia, state IT workers are flagging keywords in emails related to coronavirus that are coming from outside parties that could be phishing attacks, Chief Information Security Officer Michael Watson said.
“A lot of these malicious parties are trying to play on your fears and have you make a rash decision,” Watson said. “They’re saying that there is some immediate action you’re going to have to take to protect your own life and safety.”
Criminals often prey on people during natural disasters or crises, exploiting uncertainty and fear. But the difference with coronavirus, cyber experts say, is that the information is constantly changing, and new warnings are expected to be issued for weeks — or even months.
Scammers already are selling bogus products online, offering vaccines they claim will cure the virus or asking for donations for victims, the Federal Trade Commission has warned.
Hackers, too, have gotten in on the action, aiming to steal victims’ usernames and passwords or plant malware that will help them get ahold of other personal information.
In one phishing campaign, cybercriminals sent emails that look like they came from the World Health Organization, asking people to click on a malicious link to view coronavirus safety measures.
Last Friday, the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency issued an alert warning people to be vigilant about phishing and other scams involving coronavirus.
Phishing attacks can be lucrative for criminals. In 2018, victims of phishing or similar attacks lost at least $48 million, according to the FBI’s Internet Crime Complaint Center.
“We’re seeing them exploit this highly topical thing called coronavirus,” said Ekram Ahmed, spokesman for Check Point, a global cybersecurity company. “It’s not uncommon for certain events to be exploited. But we found it far exceeds anything else, in terms of malware.”
Malware is malicious software that infiltrates and damages computers.
Check Point found that 3% of the more than 4,000 coronavirus-related domains registered globally were malicious — a 50% jump over the industry average of 2% for these types of cyber threats. A domain name is the address of a website at the top of a browser window. Many of those malicious domains probably will be used for phishing attempts, Ahmed said.
“That’s extremely alarming to us,” he said, noting that another 5% of the domains were considered “suspicious.”
Check Point recommends that people be cautious about opening email and files received from unknown senders and beware of look-alike domains that actually are phony websites.
Proofpoint’s Kalember agrees that coronavirus-related email threats have been ramping up.
“It started out as a few small attacks. Each day we’re seeing larger and larger amounts,” he said. “Over five weeks, it’s into the millions of messages.”
People most likely are clicking at an “incredibly high rate,” Kalember added, because the volume of attacks is spiking, and cybercriminals wouldn’t bother if it wasn’t effective for them.
State and local governments need to be especially careful of coronavirus phishing threats because they can lead to ransomware attacks, according to Kalember.
Ransomware typically spreads through phishing emails. It can hijack a governmental computer system and hold it hostage until officials pay a ransom or restore the system on their own.
Last year, there were at least 113 successful ransomware attacks on state and local governments, according to global cybersecurity company Emsisoft.
“State and local governments should be paying more attention to email,” Kalember said, “and making sure their staff knows that coronavirus communications aren’t going to come in a zip file or Word document that they’d click on. Their people should be trained to look at things skeptically.”
———
©2020 Stateline.org
Visit Stateline.org at www.stateline.org
Distributed by Tribune Content Agency, LLC.